MassTLC Keynote Presentation


On 6 October, 2016 I gave the following keynote speech at the MassTLC D3: Data, Development, & Drive Software Dev Conference. The full video is available on my YouTube channel.

Good afternoon. My name is Andrew. How are you? Everyone awake? Enjoy Lunch? Good. If I put you to sleep, I’m sorry. Alright, let's get into this.

The 25th of January 1999… Anyone remember what happened this day? Besides the impending doom of Y2K setting in and realizing we have less than a year to go.
'
Scott McNealy introduced Jini, which is the java networking interface and his whole idea was that everything should be on the internet all the time. Everything should be networked all the time. And he also said something else, but no one remembers anything about his press announcement. No one remembers anything about Jini. No one remembers anything about the technology.
All they remember is that he said, “You have zero privacy anyway. Get over it.”
That’s what everyone remembers from the entire event. I’m not quite sure that’s what he hoped would happen, but it’s what stuck.
What he really meant was you have no security anyway. You really have no privacy anyway and that privacy is contextual. What people think of as privacy is, “I want my privacy,” but they want it from specific facets of their lives, not privacy from everything. Otherwise, you’re a hermit who lives in the woods with an outhouse. You have no security. This is really foretelling in 1999 to come out, and we’ll start going into how this happens.
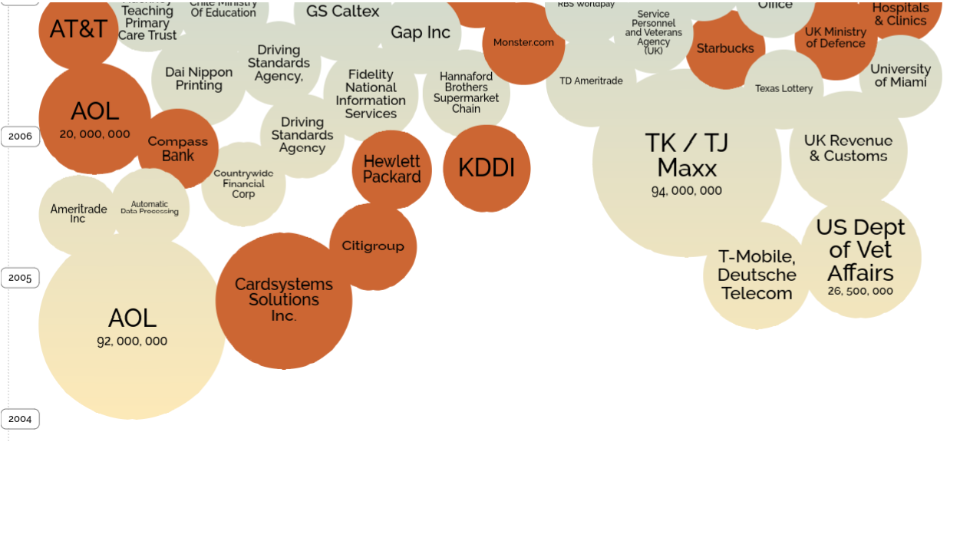
So back in the heady days of 2005-2006, we had just a few data breaches. The size of the circle matches roughly the size of what was leaked. In 2005, we have some more, 2006 we have some more. This is ten years ago. We must have gotten better. We must have figured out that after the first couple of breaches things need to be tied down, locked up and secured.

Not so much. Over the subsequent few years, we had more breaches and they got larger and they got more devastating. And they happened across more companies and more countries. Most of this is U.S. focused, but it’s still everywhere. When the U.S. Army, various U.S. law enforcement agencies, Department of Defense, the military… when these start becoming open targets and having their data leaked, you know something’s very wrong. You would think that they would spend all the money in the world to protect their soldiers. However, it keeps going.
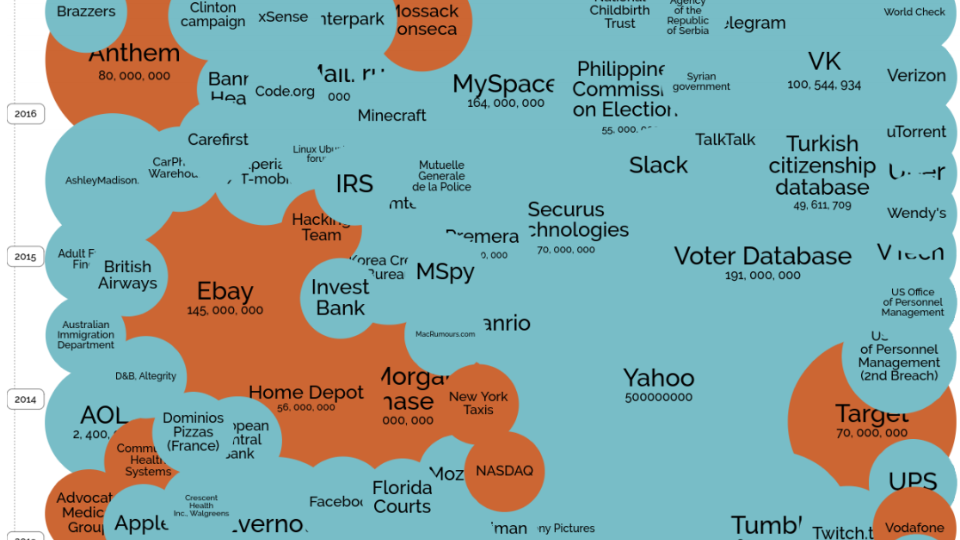
This is the past two years alone, and we have Yahoo, which just came out, it turns out it was actually 2014, there’s five hundred million accounts. Voter databases, it gets more and more critical, more and more healthcare, less financial, or just don’t think because the information wants to be free, or so people think.

We invented new things. This is a lightly censored image of Pornhub on a refrigerator at Home Depot. So people always think that, refrigerators and other things must be running some secure operating system. They can’t possibly run common everyday web sites. On the one hand, Pornhub has worked so well and it works under, like, this is basically a mobile environment. I’m sure they did that for their target customer. At the same time, your refrigerator is now running a full mobile operating system that is just as infectable as everything else, except how do you update it? You are totally dependent on, just like your phone, you are totally dependent on your provider to provide you updates. I don’t know when Samsung will roll out the anti-Pornhub feature on their refrigerators, even what they see from, no offense people of Samsung here, but given the reaction to the Note 7 response and the fact that one just blew up on a plane yesterday, I think the tech industry as a whole needs to learn about recalls and how to do them quickly and safely.
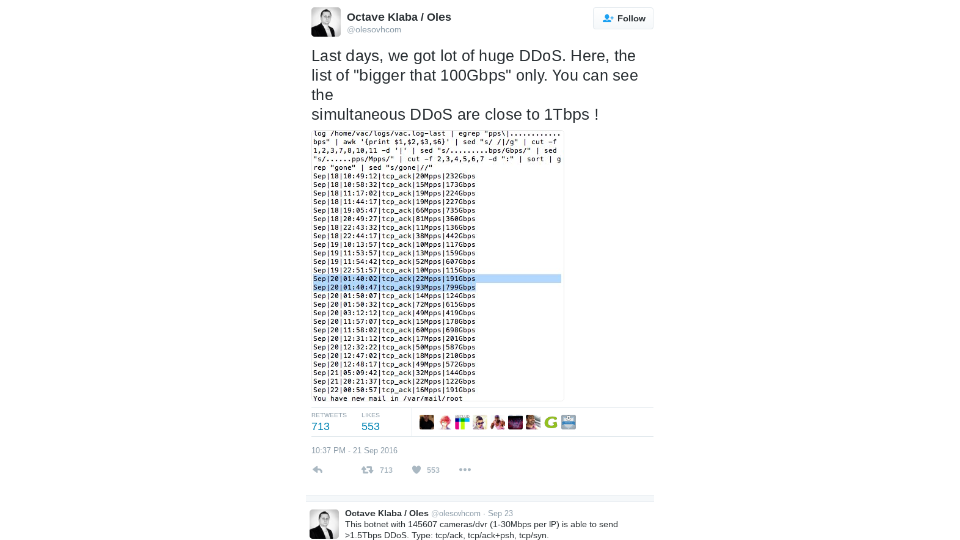
What happens when your refrigerator doesn’t run Pornhub and instead has default credentials and participates in an attack on another web site? Krebs on Security is a security blogger. He spends most of his time going into the dark corners of the internet and then writing about it. So naturally he gets a lot of people who don’t like him and then attack him. What you have here is basically an 800 gigabit DDoS against his web site and people reported a gross of over a terabit. This is the largest DDoS we’ve ever seen and I also find it hilarious that a command line is still the easiest way to get this data. No matter how much you have, you can do hideous piping commands in bash to get the format you want. It’s faster than trying to do it in a graphical environment.
So what happens? Even Akamai throws up the white flag and says, “We surrender.” They hosted Krebs on Security .com for a long time. They’ve done DDoS protection for free, and now they basically just said, “Look, we give in.” A terabit DDoS started affecting internet exchanges, started affecting their customers and it cost them a lot of money to provide them cover and, they basically said, “Well, you need to leave. We’ve become such a huge target. We’re under attack all the time.” This is a horrible situation. You, as a company right now, under the thumb of some guy or woman with a botnet under control of 145,000 security cameras. We’ve always heard that security cameras, they’re insecure and no one changes the passwords, anyone can take them over, but they run such a minimal operating system, no one could ever do anything bad with it. Well, they just exploited TCP to do SYN-ACK, force a response, send the response somewhere else. It’s a basic denial of service attack. Do that with 145,000 cameras across the world and you’ve now just taken out a website and potentially put a multi-billion dollar business at risk.

Are we innovating? It’s sort of a rhetorical question. The criminals are. The criminals are innovating far faster than we are. And how they do it and why they do it and how easily they do it has been sort of fascinating for me for the past couple years. Looking into cybercrime, looking into transnational organized crime, how quickly they come up with ideas, implement ideas, work together… criminals are criminals. For the most part they will backstab each other, they will sell each other out, they will turn each other in to the police, they will cheat each other, everything you can imagine they do to each other, yet they still seem to get stuff done faster than we do.


The stories like this come out. Cybercrime is the Next Entrepreneurial business path. If you could figure out how to legitimately turn your cybercrime organization into a real company, you could make a lot of money at it. You could out innovate most cyber security companies.
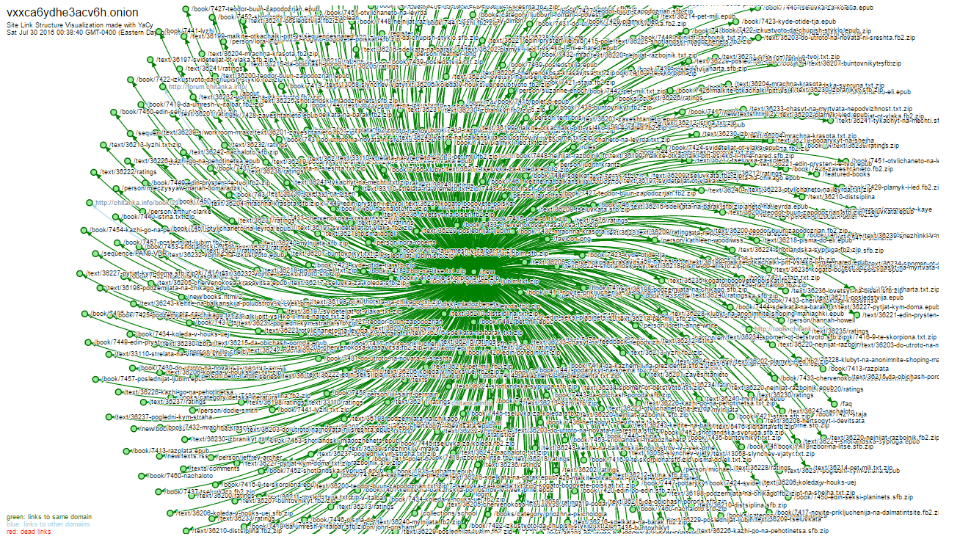
Here is an example. This is a dark net tor .onion site. I’ve been doing research into dark net for two years now, just exploring it, seeing what’s out there, indexing it. And this is an eBook site. All the DRM is stripped off all the eBooks. There are a couple hundred thousand books here. This alone should not surprise anybody. Anyone that’s into hacking could strip DRM of your eBooks and get it for free. What’s interesting is that who they link to, in that this is on Tor so you need Tor to get to it. It’s a .onion. It doesn’t exist in the clear web, yet they have all these links to all these other public sites. The most interest one is this one over here. The python book reader. They will let you read all their eBooks for free – just to highlight that. They will let you read all their eBooks for free if you go to this website. When you go to that website, you get served ads in your book reader. So they are profiting off the ad networks as you read your free books. They don’t actually charge for books, which is interesting in itself, probably because no one would pay for it, or you wouldn’t trust any payment system they have, so they use ad displays as their payment system. Also interesting is that everyone thinks cybercriminals are some mastermind. They went to Bulgarian Wikipedia. Because when you go to Wikipedia.org, it defaults to whatever your native language is in your browser, so most likely they are Bulgarian.
Let’s go to a more calmer time. This is me at ten years old. I had just been through computer camp and I had no idea what the heck I was doing in the world. Obviously it’s 1981, you know, the super cool t-shirt.

This was one of the first computers I had. This is a DEC Rainbow. It was the revolutionary personal computer that everyone always wanted. It had two different processors in it, the super cool floppy drives and the six inch screen that – I think our phones are bigger than this screen is now. Our phones are definitely far more powerful than this whole computer is.
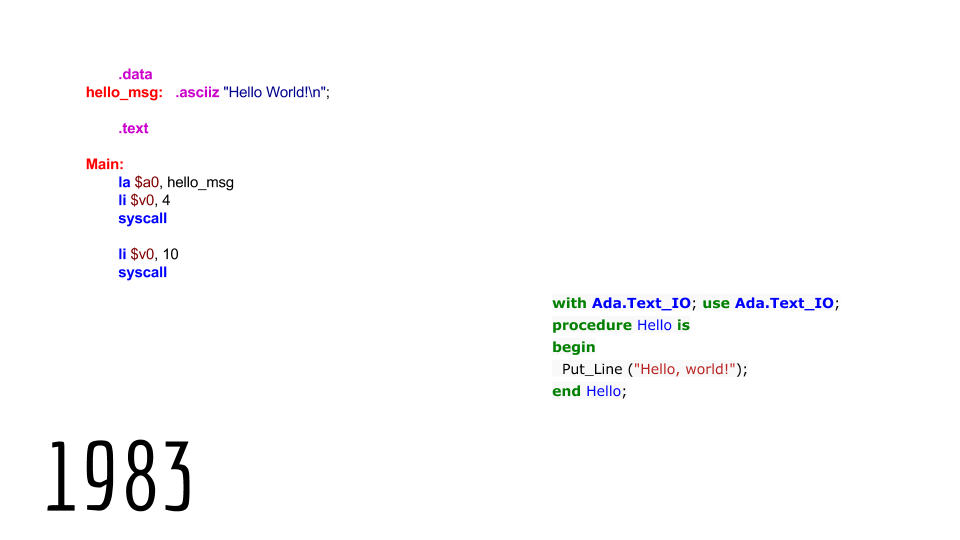
These are the first languages I had to learn. My father was an electrician in the Navy. We spent a lot of time in Kansas and Arizona. You might think that there’s no ocean in Kansas and Arizona. He had top secret clearance and, to this day, I only know he was an electrician. Yet, I had to learn Assembly and Ada as my first programming languages. Most people had to learn Basic. Most people’s first programming languages involved Peek and Poke on Atari and learned Basic to make the computer make silly noises. This is Ada. This was the government language that came out in, like, 1979-80 at the time. And that’s RISC Assembly. I have since forgot everything I’ve ever learned about Assembly and Ada.

This was the internet. Network connections were through acoustic couplers. You dialed in at 300 bits per second – not kilobits – 300 bits, but then the DEC Rainbow is about as powerful as that modem was, and you would type your little command and wait for it to appear on the other end.
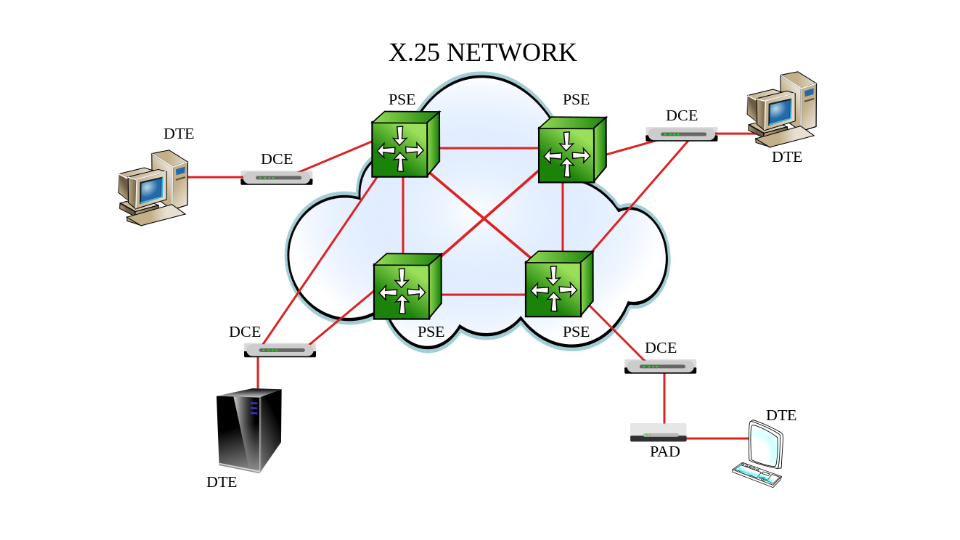
However, it gets you into X.25 networks. Before the internet was really big and popular, X.25 was what all the providers used. There was no security. Everyone was trusted. All these companies were trusted and when you unleashed a 14 year old on X.25 network that’s wide open, I met the FBI at a very young age who had no idea what I did. All they know is they had some access log that said someone from my mainframe account – because you're 14, you don’t think like this – I had logged into my own account, used my own account to get into to all these other companies’ stuff, and explore their systems. And apparently someone noticed because I explored a defense contractor system who is the only one who had auditing on to look at log-ins. I didn’t tell them, “Well, actually I connected to 40 other people, but you just caught this one, so, yeah, that’s what I did.” It’s often not a conversation you want to have with your parents.

So as Mike said, I went to Westborough High School. I went to Framingham State University, not college. And, what I went to school for, was biology. I was always interested in neurobiology and behavior. What’s the bath of chemicals in your brain that makes you do things? And I still am, but computers paid vastly more. So I did that.
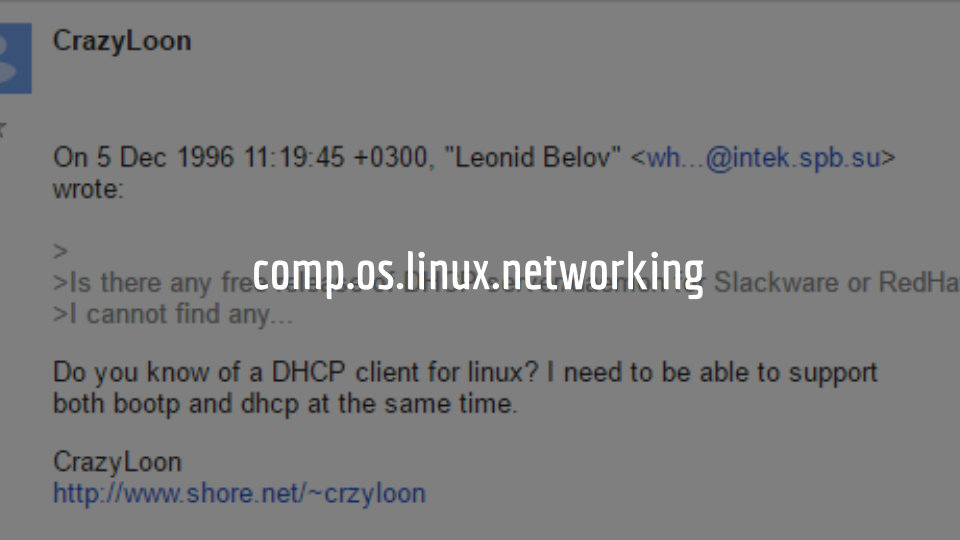
The oldest post I can find, because everything on the internet is forever, is this. One of my nicknames when I was exploring X.25 networks was CrazyLoon. And this is a news group, not a mailing list, but if you remember news groups, this was back before Linux had a DHCP client. TCP/IP was still not a thing. You still had to install a TCP/IP stack to figure out how to connect to this internet thing. And there’s my innocent, “Hey, I’m into this.”

So, I since went on to work for a bunch of companies in Massachusetts. TechTarget – I was one of the first employees. Analog Devices – I was definitely not one of the first employees. But all these places are in Massachusetts. Tor – we started in Massachusetts – it’s grown to what it is today. I left about a year ago to go work for a slightly different company.

Here’s what I do today. Farsight is real time DNS intelligence. It’s a California company but I won’t mention that too much. I work locally. Laxdaela is my own consulting company for exploring the dark web, so when I run into law enforcement, I have a company between me and them, which doesn’t really help much actually. Thorn – I work with them to do analysis of human trafficking. Emerge is domestic violence. Each One Teach One is recent in the past two years to help train women and girls in technology so that they have better options in life beyond just working at McDonalds or Dunkin Donuts or getting married. Which those are all fine career paths if that’s what you want to do, but many of them would like to have a stronger career path and be able to have the ability to learn technology and, make far more money than a part-time worker.
Through all these companies, I travel around the world. I used to spend a lot of time in Sweden. Sweden’s start-up culture is very different that Boston, which is very different that California. Sweden is socialized government. Everything’s taken care of. Some people take far greater risks. If you think California has some crazy start-ups that make no business sense whatever, Sweden also has those, except their very polite about it and very professional about it. And they’re an engineering culture so everything is designed to the 27th degree, which is fantastic when you want to drive their cars or take their public transit, but when you just want to watch a video on the internet, you probably shouldn’t have to install 27 pieces of software to get the look just right.
Innovation. What is innovation? Why are the criminals so good at it? Basically, it’s new ideas. They don’t come constrained with all these laws. They don’t come constrained with preconceived notions. Most criminals come constrained with simply, “I want to make money. How do I get there the fastest?” Conveniently, that’s how a lot of cyber security companies start as well, is, we protect something, but I also want to make money at it. So they’re not that vastly different.

The other idea here is that, innovation is always some poor person sweating away in a lab for years and decades to come up with an idea. That’s a myth. That’s a fine myth by people who succeeded because they seem to forget their entire team. You need an entire team to innovate. Having you, just you, you're stuck in your own blinders, you’re stuck in your own head. You need to be able to get out of your head and get differing opinions about them… diversity helps. Having diversity of people who all grew up in North America gives you far less diversity than people who grew up all over the world or who travel the world and talk to people. The iHub in Kenya is fascinating because the way they think about problems, I would never think about that way. And it’s mostly because I come from Massachusetts. I come from a western culture and when you go to these cultures, or when you go to Russia and China, they have very different ideas. Things that you would not even grasp of how to approach things, and you get it. You can learn quickly, but the point is that the sheer diversity and the difference of cultures is what matters. It helps you innovate far faster.

For example, here’s five people that were thrown together. Alright, six people that were thrown together for a hack-a-thon where we were the winning team. We met each other that morning and we put together a mobile app for the World Bank. The idea was everyone had very different skills. They all came from different parts of the World Bank around the world and we came up with a simple app that seems really simple in the forefront but no one had thought of it when we first started. And we’re all trying to sort of develop towards the exact same goal and we were the ones that won it because we just came up with this creative solution that the World Bank has been looking at implementing.
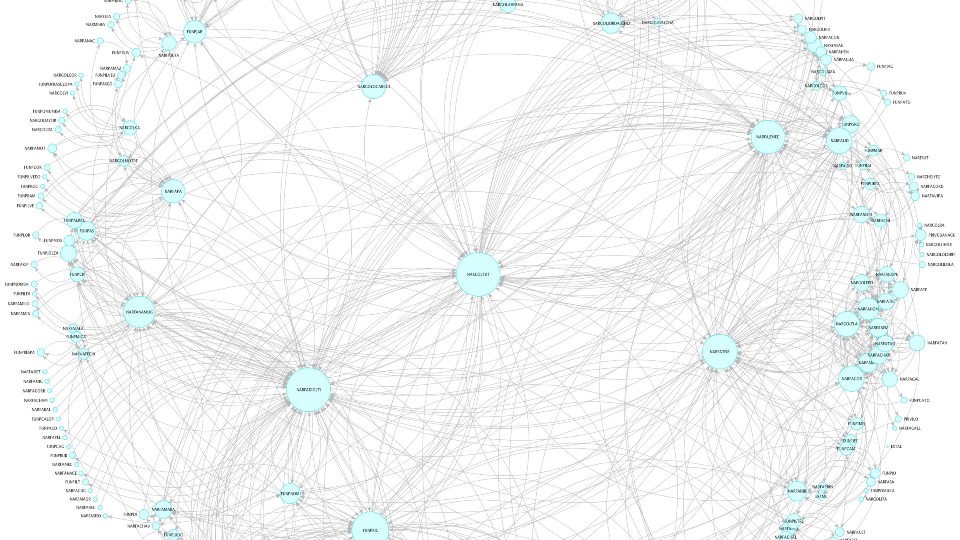
So, innovation, diversity of cultures, diversity of ideas, and moving quick. This is a criminal network. You’ll notice it’s not highly structured, rigid, or anything like that. These people work together – this is actually a drug network – but everyone works together. They all work with each other. They all connect into each other. Sure, there are some people who call the shots who have more, connections that others, but they all seem to work together and they all just get things done. They all move incredibly quick. Having explored the darker parts of the world with law enforcement, you realize how easy it is to do criminal activity.
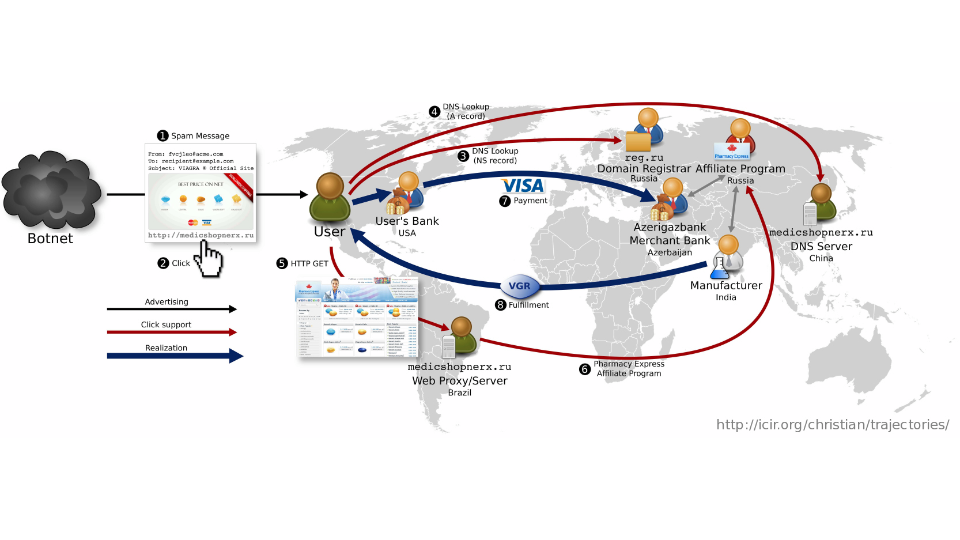
In order to make this work…, let’s take this as a criminal. As a criminal, someone steps up and says, “Hey, I just want to do this.” This is to serve nonprescription drugs and ads across the internet. It involves email, websites, and payment networks so this is the global network that a criminal network will do. It will use a botnet to spam all the ads and then you can see the advertising to click support and realization. Each of these people are stratified just like billion dollar company. Everyone has their job - has only one thing to do. And they don’t even all speak the same language. They use Google Translate a lot to figure out how to speak between different cultures. They don’t all know each other. In many cases, that’s by design because the deniability to say, “Well, I don’t know who this guy is. I just know I send it here.” In order for a legitimate noncriminal company to do this, think about what has to happen. I’ll take my own Farsight Security – when we want to work with a partner, the first thing you have to do is sign an NDA. So both have to sign an NDA, legal teams have to review it. That takes a week or so or if the legal team is fast, it’s within days. Then you have to sign a Master Services Agreement. Then you have to sign Partnership Agreements. Then you have to haggle over reselling and rights and all this stuff. All this stuff takes, anywhere between a week and a month to get done with any smaller company. Larger companies – I have contracts that are still in the Master Services Agreement phase, which are nine months waiting on legal to go through it. If we were a criminal enterprise, we’d be broke trying to do this stuff. Criminals will set this entire thing up in under two days. There are no agreements. There’s no legalization. They just move fluid, fast and they also rip each other off, but they do end up making money. Everyone has their role, everyone makes their money.
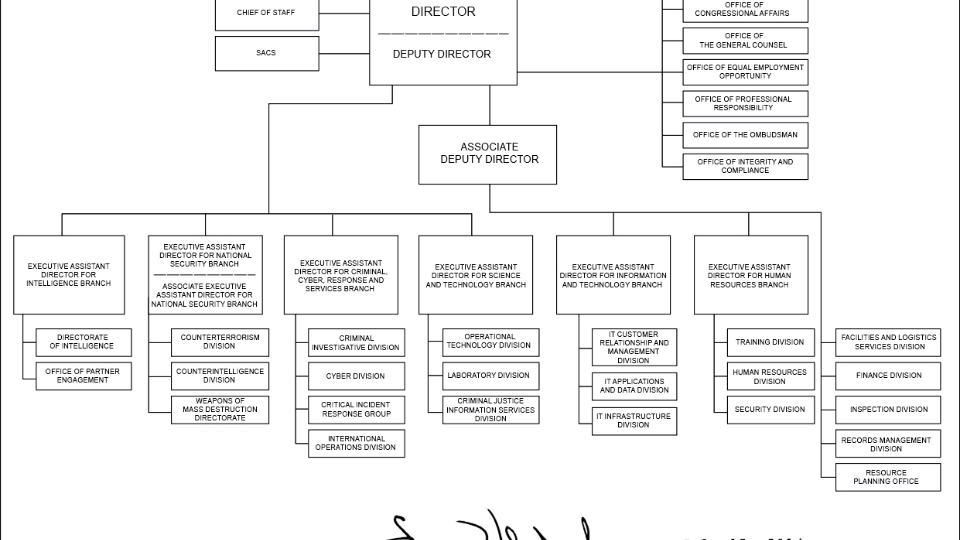
This is how the FBI approaches cyber-crime. I pick on the FBI because I work with them a lot. But it’s highly structured. Everything has to go up or down, mostly down. And there is not a lot of cross-functionality, cross working together. This is in vast difference to what you saw with the criminal networks that are just everywhere. And the innovation here is really in PowerPoint in moving one division to another, as opposed to getting things done, getting technology adapted. The FBI and most global law enforcement has picked up quickly. Cyber Division is almost a quaint notion now because every crime involves cyber. Having just people who are cyber experts is fantastic but now you have cyber in every criminal investigation because no criminals stay away from the internet. There are no offline criminals anymore.
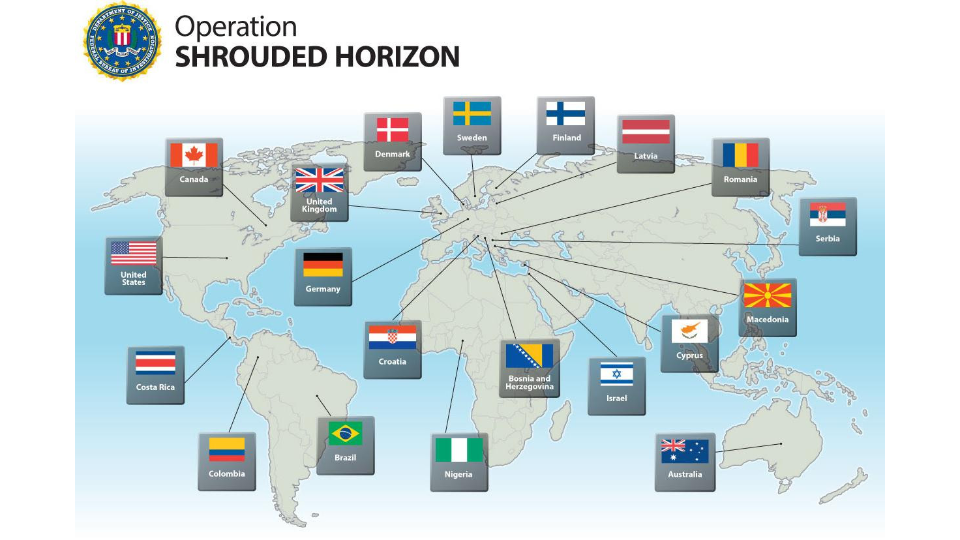
Here’s an example of innovation. Operation Shrouded Horizon took down Darkode. Darkode is a carders forum where they, all these carters around the world got together, they all decided they were going to speak English or Russian, so there’s a lot of Google Translate and horrible translations. But, they got together, they hosted a forum. It was called Darkode. It could not be any more out in the open. It’s hosted in Russia, so, most people wouldn’t take it down, and global law enforcement got together and this is innovation from a law enforcement perspective. They work with commercial companies and all these different countries to take down the website, identified it, the people and take down the big ring to hopefully take down the entire forum. So there’s a lot impressive about this. They took it all down. They did a great job. It’s about a two year operation and then two weeks later…
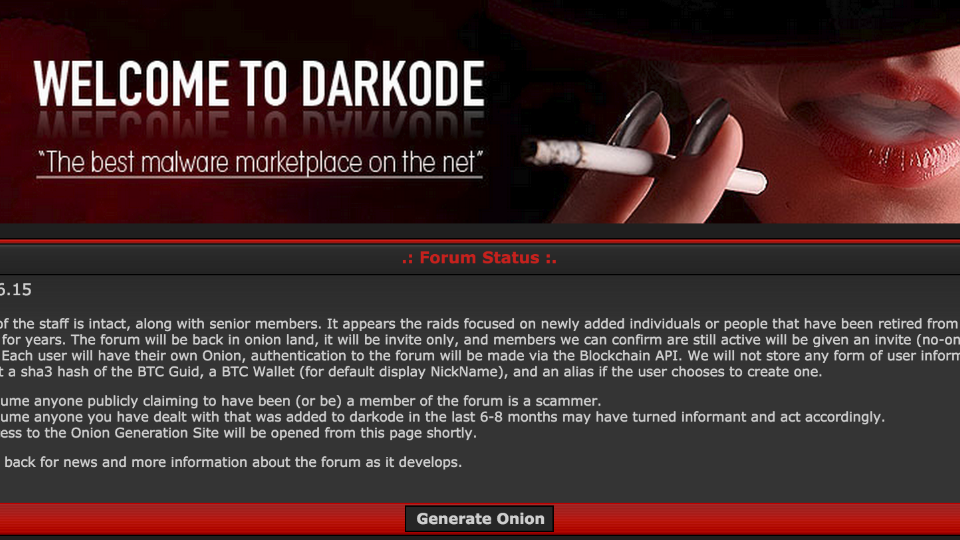
It pops back up because the criminals who didn’t get caught said, “Well, now we know what not to do. So let’s innovate.” And they moved everything to Tor – so this is actually a .onion site. They moved to tor and then law enforcement was sort of, like, fantastic. Now what do we do? And so what they did was they go back to investigate everything. And the point was that the admins of the site took it – it took a week for them to figure out how to reset it all back up, make all the connections they need for all these parts of the operation and, get back online and get back in business, which they did.

On that depressing note, we have locally, according to Xconomy, we have 67 cyber security companies in this area. They are raising tons of money. They are all doing well. They’re in various sizes from start-up to large enterprises. They all focus on different parts of the cybercriminal chains. Some are global, some are endpoint protection, some are data analytics. So we are innovating. We are making change.
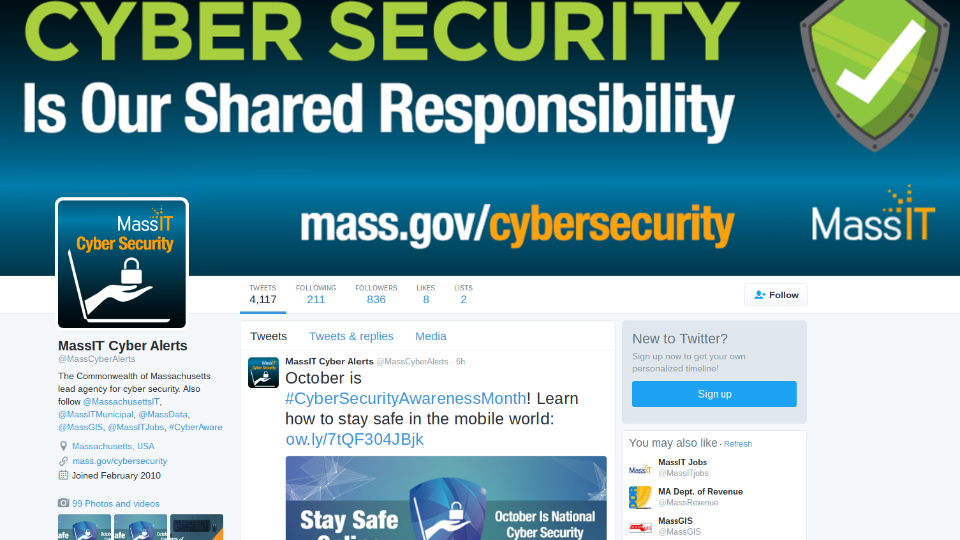
The state has actually gotten into it. The state has its own Twitter feed. Did you know October is Cyber Security Awareness Month? I actually didn’t know that. On the one hand, this is fantastic. I love that Massachusetts has this and it’s out there. Not too many people follow them. They’ve got 200, err, 800-something followers out of a few million people in the state. And it’s also, on one hand, I love it. On the other hand, it’s the most depressing feed ever because all it is is breach, breach, breach, exploit, breach, breach, exploit, breach, breach, breach, exploit, how to not be a victim. And it’s great that we have it. On the other hand, the news is just so depressing.

What do you do? A lot of what you see in the press is that, the Russians are hacking the election allegedly. The North Koreans broke into Sony and you have nation states coming after you. I’m not going to survive the attack by any nation state. I don’t care how small it is. This is North Korean Army. They have their own cyber teams, just like we have our own cyber teams. This is nation state stuff happening on the internet against companies. An individual company is not going to survive an attack from a nation state. If you’re targeted by the NSA, let’s say, you’ve already lost. Before you even realize it’s the NSA, you’ve already lost. Now imagine that' similar for other agencies out there and our not-so-friendly enemies and you’re in deep trouble.

Here are the four you see in the news all the time. On the upper left is the Chinese Ministry of State Security. They are the overall agency who has cyber teams in universities and stuff doing nothing but hacking, PLA, all that. On the lower left is the Russian SVR. They are the foreign intelligence service. They are another overarching agency that has activity for all sorts of attacks. In the middle is the Iranian Ministry of State Security but it’s somehow it says MOIS, and they are also blamed for a whole bunch of stuff. And then on the right is North Korea and their cyber teams are all attacking you.

When you look at the media, it’s almost always some lone hacker who does this stuff. Much like the myth of lone innovators, it’s never a lone hacker. They always have support. They’ve always stratified. Anyone who is a lone hacker is trying to show off and then will get piled upon by all the rest of the criminals who are like, “Well, I could do that better. I could do this better. Why’d you cut me out of the deal? What’s going on here?” This is actually the friendliest hacker I could find. Usually it’s some dark shrouded face.

The real risk, though, regardless of what the media says, is your partners. As a company, these women are like, “Fantastic. We just signed on with these two guys. We’re going to make tons of money off our partnership.” What they don’t realize is these two guys have no firewalls, have no security, because they think it’s just a cost center and there’s no point to paying for any of this stuff. What their risk is now is that they still have the connection, whether it’s over the internet or they actually pull physical lines like banks do between each other. Your security is now as secure as that line is, and that company behind it. How risky are they? Where have your partners’ IP addresses shown up? If your partner’s IP addresses and their network constantly show up on the affected malware list or whatever, that should be a red flag to you and say, “Hey, you should clean up your stuff. Or you should charge a lot more. Or you should take out far more insurance for when you get breached because something comes through them.”
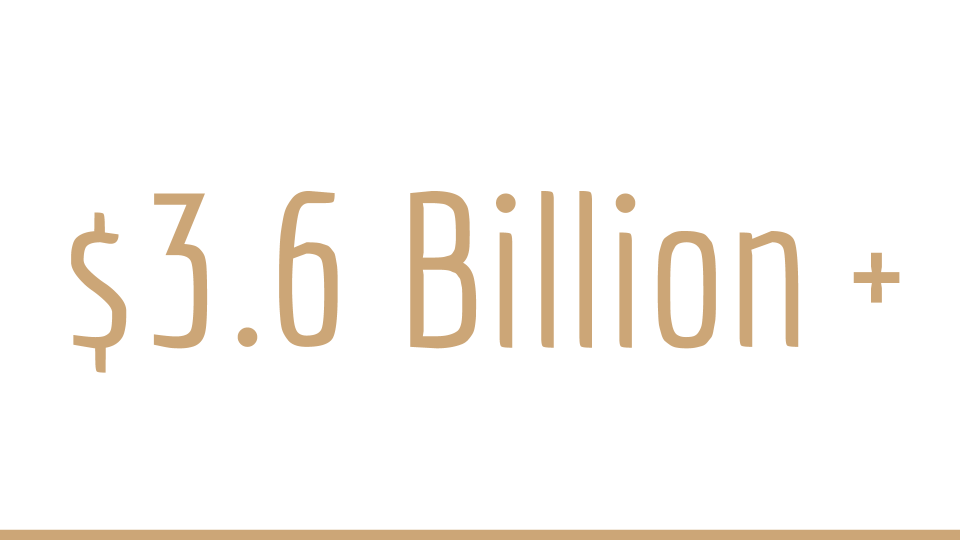
These 67 companies have raised $3.6 billion. That’s a lot of money. And typically in, we’re not going to use the war terminology here, but both sides, the criminals are raising this much money too. And so we have to raise this much money to fight them. And this is where, there’s plenty of venture capital. There’s plenty of money out there where people are looking at it saying, “What could we do to fight this?” And, you know the venture capital approach is to put their money in a bunch of pots and hope one of them wins. Maybe two of them win. If they’re really lucky, three of them win. Otherwise, the goal is to just put the money, let these companies see what they can do, see who innovates and the ones who innovate may win or at least get a client.
There is a lot of press about Massachusetts and cyber security. We are doing a lot great work. There’s an actual cyber security commission – The Advanced Cyber Security Center – that does a lot to try to get, just networking, just like MassTLC started to focus on getting people together. Xconomy has a lot of articles about this and people are moving to Boston, which is contrary to what many people think. I almost wonder if more people move to Boston in the spring or if they move in the winter. Because if they move in the winter, you really want to be here.

Innovation takes a community. In order to do this, as I said, you need product managers. It’s not just a lone avenger with some brilliant idea. That helps, but then they need product managers, developers, coders, designers, all this stuff to work together to build a thing. This is exactly how cybercriminals work. A criminal says, “Hey, I got an idea. I got an angle. I need someone to do distribution. I need someone to do the design. I need someone to make me a web page. I need someone to handle processing payments.” You need all this stuff to innovate. They naturally go wherever they can find people to work with. So they tend to be far more global and have far more diverse opinions and this is where we’re at now, or we’re starting to get there.

Cyber security companies are getting there and we are that community. Everyone here is part of that community. We all have different ideas. We all have different specialties and expertise and we should all use them to work towards the same goals, whatever your goal is. You know, my background is cyber security, but, there’s robotics, there’s insurance, there’s financial technology. There’s all this stuff that having innovation, innovation comes from a thing, it comes from us. It does not come from any one person who you have hopefully hired some brilliant person out of college.
And that’s it. Thank you.

Are there any questions, thoughts, concerns?
Q: When you started working with the FBI again, did the bring up the thing when you were fourteen?
A: No. Officially that goes off your record because you’re a minor. I believe back then because it’s in paper, it probably is off my record. But now if you’re caught, even if they say it’s off the record, I guarantee everything is saved forever. Because why not? It’s just bits.
Q: Distributed innovation on the cyber security side? Is that the solution to deal with the kind of innovation that’s happening on the criminal side?
A: I think …
Repeat the question please.
Q: Is distributed innovation in the cyber security side where we should be going?
A: I think, yes. I think it’s worth trying. I think it’s worth it. I work for a distributed company. Tor is a distributed company. It’s incredibly hard to run a distributed company because of time zones, because of cultures, because of language and because video technologies is infinitely infuriating. It never works when you want it to. It never works how well you want it to, but chat, phone calls, all this stuff still works. It still, when you look at productivity, the most productive times, both at Tor and at Farsight are when we’re all together. We have company meetings. We meet somewhere in the world and, having 30 people in a room gets a lot more done than distributing endless email and chats and all this other stuff. Phone calls and all that. But I think that having the diversity of opinion is fantastic and having the different cultures and experiences of what people think, how they think about a problem, help innovate far quicker. And so as long as you come into it with an open mind, and say, “Here’s what we’re going to do and here’s how we’re going to try it.” That’s what seems to work well.
Q: How do you think Cloud computing conflicts…
A: How do I see what? How do I see Cloud computing? Cloud computing is just someone else’s computer. No offense to Cloud companies here. It’s distributed. It’s a cloud. Sort of the same way as you would secure your own infrastructure or your data center is the same way you should think about Cloud. Some of that is also risk management. You’re going to put your files, you’re going to put your core sensitive data on someone else’s network and you hope that, they have insurance and they’ve gone through those practices or even better practices, to secure your data so they don’t accidentally leak it. There are a lot of companies, two of which locally, who have been working on Cryptzone and they’re still working on, sort of, it’s on the Cloud but it’s in your secured container. And you can then move that secured container somewhere else if that server goes down or gets breached or whatever. But there’s more innovation needed there.
Q: Do you see advanced encryption as a force for good or a tool for bad?
A: I see it as both. So I was at the Aspen Institute Cyber Security Summit yesterday. And it’s interesting because the NSA repeatedly said that encryption is really not their concern. They sort of see it going spotty, but otherwise, they’re not worrying about encryption. And the FBI repeatedly said encryption is our nightmare. Encryption constantly stymies investigations and makes us go dark. So going spotty versus going dark. On the one hand I take that to mean the NSA is not worried about encryption because it can break it, and so they’re not going to actually say that. I mean, I wouldn’t say that, or it’s just posturing so that when, like the Russians and the Chinese say we’re heavily encrypted, make them, it’s a whole psychological operation there. But the FBI has been pretty clear that encryption, you saw the iPhone thing. They constantly run into it with these technologies that are heavily encrypted end to end, and, in some cases, the user of a device doesn’t know the passcode to unlock those things. It’s tied to two factor authentication, or three factor or four factor, and so it does get in the way of law enforcement. However, there’s plenty of other ways, other countries who are less moral would just put a gun to your head and say, “Type the password in, and if you don’t know, we’ll throw you in jail until you remember it.” And, for the business side though, everyone wants to secure their information. Both the NSA and the FBI have come out and said, “We want you to have strong encryption.” I mean, the director of the FBI encrypts his laptop when he travels. He’s the director of the FBI. I mean, he doesn’t have to worry about border crossings and that, but he still does it just because it’s what you’ve heard, encrypt your laptop. So most likely your laptop is going to get stolen, not someone hack in to it, so if it gets stolen, at least it’s encrypted. I think that encryption still has a long way to go. I think that quantum encryption is really where the next thing is going to be at. It’s still in its infancy, but it’s vastly stronger and vastly easier to implement. Right now, encryption is really CPU and memory heavy. It takes a lot of power to do that, even with your phones, it’s tough to do that. And if you’ve encrypted your phone, you notice it’s slower. It’s demonstratively slower because it’s got to do all of these calculations all the time. Quantum crypto does much quicker and much smaller bit sizes so you can do things far faster and once you have Internet of things using Quantum crypto, heavily encrypted, talking to each other and serving up Pornhub, then you both have a panacea of a group model and a nightmare for law enforcement in trying to secure your devices.
Q: If cybercriminals are acting more like corporations, to what extent are corporations acting more like cybercriminals?
A: The questions is: If cybercriminals are acting more like corporations, are corporations acting more like cybercriminals? Yes, in that I have worked with a number of companies who basically, you meet someone, you meet them in an investigation, you meet them in conference, you just call them up and say, “Hey, we see this. We need your help.” Magically, a handshake is still what it takes to get most business done and then the lawyers get involved and then all these papers get signed. But, for the most part, if you have an active thing that’s time pressure, companies will work together and they do, it’s very much like the cybercriminal world where you meet, you talk, you say, “Here’s what we’re going to do,” you assess that you can trust the person or not and then, if you do, you move on. And you start working together and you start solving problems. This is how a lot of law enforcement operations work, is that before all of this stuff happens, the breached company or the infected company, or the company that needs help, will reach out to whoever law enforcement officers they know and say, “Hey, we need some help. Can you come help us?” And then the lawyers get involved and then a lot of stuff that happens afterwards, but usually it comes down to the individuals to make the contact. If they trust each other or not, and if they do, they start working together quickly. So that does help to take down criminal activity very quickly.
Q: Where do you see the or is there a merge or is there a future in merging of cyber security and digital forensics? Like, they’re now one thing or is it two separate…
A: So the question is where do I see the merging of cyber security and digital forensics? Digital … Have any of you read the PCAST Report? No, of course not. It’s a presidential commission on science and technology. They just had, it’s a long report about forensics where they basically said a lot of the forensics today are not scientifically proven and digital forensics is the number one field they said is just a total mess. I think that as… people need to understand computers, they need to understand what’s going on inside the computer, for whatever type of computer it is: phone, desktop, servers, Cloud, whatever. And as they start learning more about how this stuff works and the traces you leave behind, that digital forensics will get much better and will be repeatable. Most of the problem that the presidential commission identified is that it’s not repeatable, and you can’t just simply say, “Well, we examined this hard drive and this one time, and we found this data on it. So therefore, that proves whatever.” And in the court’s view, the commission’s view was that you need to analyze the same hard drive, the same time, the same way a statistically significant number of times, get the exact same results, then it’s scientifically proven. Not just once. And who’s to say that when you clone a hard drive, you didn’t change the data. Who’s to say when you went to read the hard drive, or whatever device it is, the memory, just by reading, you changed the state of the data. And that’s a lot of what the affect is. So I think that we’ll get better at it. Right now, it’s all forensic labs are buried under an avalanche of data and they can’t keep up with the requests. And this is why you see… I’ve worked with even the FBI’s forensic lab or the State Police forensic lab will say, “Yeah, we’ve got a one year backlog.” And, so this is why your court cases take forever, unless you’re willing to pay. There are financial companies who will say, “Great. If we pay you $20,000 could it be done this week?” And the answer is almost always yes. You go to a commercial lab, you have them do it and you give them the data and then some defense lawyer tears apart the forensics saying, “Well, they analyzed the drive just once. Do it twice. Do it three times. Prove to me it’s the same result every time.” So I think forensics needs a lot of work and will get better. I mean, what’s state of the art today, I think just basing on the presidential commission’s report is not repeatable. And from what I’ve seen in court cases, you have them bring an expert witness in, and then you come up with a huge amounts of data and with the hope that 25% of it the judge allows. And that right there should tell you that judges don’t believe 75% of what they see, at least the digital side, or they don’t understand it or both.
Q: Globally, where are the biggest centers of criminal talent and how are they being developed?
A: Where are the largest centers of criminal talent and how are they being developed? Well, everywhere is the reality. You hear about Eastern Europe a lot. You hear about South America a lot. That’s because they’re the most accessible. The drug war has improved a lot of criminal’s technical capabilities by causing drug cartels, don’t want to keep their money and everything happens on the internet today. So they’ve done a lot to promote that. Southeast Asia is another big spot because they don’t really have… they have different copyright laws and understandings of intelligent people than we do. And it’s much more fluid there. And, so I don’t want to, there’s no one name. I can tell you that in Boston there’s plenty of cybercrime that goes on. Mostly though, it seems it’s always foreign and when I go to, like, Bulgaria and places like that, they say the U.S. is the pit of all evil for cybercrime. So it’s sort of contextual where you look.
Yeah, one more.
Q: What would you say to consumers of…
A: What would I say consumers? That’s funny. I was talking about that at lunch. So I have smart thermostat in my house. From anywhere it can be accessed. From anywhere, I could come home and my house would be like 300 degrees or it’ll be frigid in the middle of winter and freeze up my air conditioning unit. However, the benefit still outweighs the risk to me. I did a risk analysis about it, I wonder if I did it correctly or not. I think for consumers, NIST just – National Institute of Standard Technology – just came out with a report yesterday that said people have security fatigue. They are so sick of hearing about breaches. They’re so sick of hearing about everything’s exploitable. They just don’t care anymore. Many companies are making the decision of to, they treat cyber security like a risk. What’s the risk? How much do we have to spend versus how much gain we would get? How much a of a pain in the ass does it make us using these systems versus, it’s far more efficient and less cost for us to do it this way, and we’ll just take the insurance hit when it comes? Mostly for the consumers, looking at my own behavior, looking at the behavior of my friends, we’re all cyber security people. We all know our credit cards could be hacked. We all know our identities can be found easily. We still do what makes the most efficient sense for us. Inherently, people are lazy. They don’t want to have to do a whole bunch of extra work. I tried to live for two weeks, when I was at Tor, and a challenge, I tried to live completely anonymously and completely privately. It’s exhausting. When you try to think about every place your information goes, every place your data goes, everything you trust, everything you could possible ever record, anything you’ve ever done, trying to avoid cameras in the center of Boston is impossible. You end up wearing some stupid hat or something to defeat facial recognition, which I’m pretty sure doesn’t work whatsoever, but it makes you feel better. And it becomes just exhausting to spend all your time thinking like a completely paranoid person, and you just, you can’t win. If someone, en masse, you can something, like, finger one of the big breaches. There’s something you can do to complain to the company. You can get some sort of recovery, at least alerts to protect your identity. But if you’re targeted by an individual, or a foreign intelligence agency, you’ve lost. Unless you’re super good and somehow managed from birth to keep your identity private, secret and secure all the way up through your current adulthood life, you might have a chance there. But even then, chances are you’re in state databases, federal databases somewhere that someone will breach someday. This comes to light for people of clearance, the OPM breach. Everyone figured OPM was secure. It’s got all the cleared people in the U.S. in it and everybody cleared, is cleared, currently cleared, where they work for and what they do officially. You would think that would be secure. That came out and now it’s believed to be in the hands of Chinese and they now have … So everyone’s like, “Well nothing happened initially.” Credit cards aren’t being stolen, my data didn’t get stolen, nothing really happened. It’s the fact that it’s out there and it’s out there forever. It may take five years, ten years, twenty years. You may go to vacation in China someday and get picked up then because they’re patient and they’ll wait. You as a consumer should make the decisions of “use what you like to use.” Use what makes the most sense for you. Be aware of, what if my smart meter company sends me an email saying, “Hey, by the way, we have a software update.” Apply the update. But for the most part, I’m going to choose the stuff that makes my life more efficient because of my high security issues. I just assume we all have security issues.
Alright. Thank you.
